What is OData?
OData is a standard protocol for creating and consuming data.
The purpose of OData is to provide a protocol that is based on Representational State Transfer (REST) for create, read, update, and delete (CRUD) operations.
OData applies web technologies such as HTTP and JavaScript Object Notation (JSON) to provide access to information from various programs.
OData provides the following benefits:
- It lets developers interact with data by using RESTful web services.
- It provides a simple and uniform way to share data in a discoverable manner.
- It enables broad integration across products.
- It enables integration by using the HTTP protocol stack.
The public OData service endpoint enables access to data in a consistent manner across a broad range of clients.
OData services
We provide an OData REST endpoint. This endpoint exposes all the data entities that are marked as IsPublic in the Application Object Tree (AOT). It supports complete CRUD (create, retrieve, update, and delete) functionality that users can use to insert and retrieve data from the system.
Supported features from the OData specification
The following are the high-level features that are enabled for the OData service, per the OData specification.
- CRUD support is handled through HTTP verb support for POST, PATCH, PUT, and DELETE.
- Available query options are
- $filter
- $count
- $orderby
- $skip
- $top
- $expand
- $select
- The OData service supports serving driven paging with a maximum page size of 1,000.
Filter details
There are built-in operators for $filter
- Equals
- Not equals
- Greater than
- Greater than or equal
- Less than
- Less than or equal
- And
- Or
- Not
- Addition
- Subtraction
- Multiplication
- Division
You can also use the Contains option with $filter requests. It has been implemented as a wildcard character. For example:
http://host/service/EntitySet?$filter=StringField eq '\*retail\*'Batch requests
Batch requests are supported in the OData service.
Metadata annotations
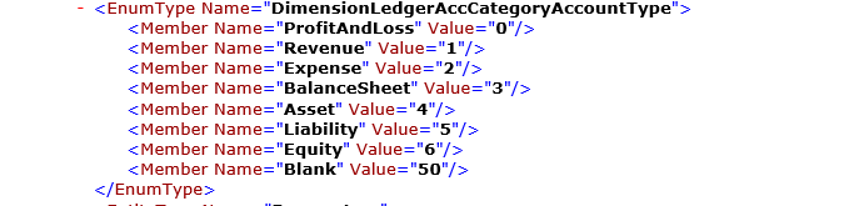
/data/$metadata provides annotations. EnumType is support in $metadata.
Cross-company behavior
By default, OData returns only data that belongs to the user's default company. To see data from outside the user's default company, specify the ?cross-company=true query option. This option will return data from all companies that the user has access to.
Example:
http://[baseURI\]/data/FleetCustomers?cross-company=true
To filter by a particular company that isn't your default company, use the following syntax:
http://[baseURI\]/data/FleetCustomers?$filter=dataAreaId eq 'usrt'&cross-company=trueValidate methods
The following table summarizes the validate methods that the OData stack calls implicitly on the corresponding data entity.
| OData | Methods (listed in the order in which they are called) |
|---|---|
| Create |
|
| Update |
|
| Delete |
|
Exposing OData entities
OData entities are based on the concept of an updatable view. When the IsPublic property for an updatable view is set to TRUE, that view is exposed as a top-level OData entity.
Setting navigation properties between OData entities
Links between OData entities are described by a navigation property. Navigation properties describe the navigation from one end of an association to the other end.
Adding actions on OData entities
Actions let you inject behaviors into the data model. To add actions, add a method to the updatable view, and decorate that method with specific attributes. Here is an example.
[SysODataActionAttribute("CalcMaintenanceDuration", true)]
public int CalculateMaintenanceDuration()
{
//do something
return 0;
}
In this example, the SysODataActionAttribute class decorates the CalculateMaintenanceDurationmethod that is exposed as an action. The first argument of the attribute is the publicly exposed name of the action, and the second argument indicates whether this action is always available. Methods that are exposed as actions can return any primitive type or another public updatable view. After this method is exposed, it appears in the OData $metadata. Here is an example.
The following example of an OData action takes in a parameter and returns a list.
[SysODataActionAttribute("GetColors", true),
SysODataCollectionAttribute("return", Types::Record, "CarColor")]
public List GetColorsByAvailability(boolean onlyAvailableVehicles)
{
List returnList = new List(Types::Record);
// do something
return returnList;
}
In this example, the SysODataCollectionAttribute class enables OData to expose strongly typed collections from X++. This class takes in three parameters:
- The name of the parameter that is a list (Use return for the return value of the method.)
- The X++ type of the members of this list
- The public name of the OData resource that is contained in the collection
After these actions are exposed, they can be invoked from the service root URL.
You can find actions that are defined on data entities by searching for the SysODataActionAttributeattribute in the source code.
Querying or browsing an OData endpoint
OData enables an SQL-like language that lets you create rich queries against the database, so that the results include only the data items that you want. To create a query, append criteria to the resource path. For example, you can query the Customers entity collection by appending the following query options in your browser.
| URL | Description |
|---|---|
| [Your organization's root URL]/data/Customers | List all the customers. |
| [Your organization's root URL]/data/Customers?$top=3 | List the first three records. |
| [Your organization's root URL]/data/Customers?$select=FirstName,LastName | List all the customers, but show only the first name and last name properties. |
| [Your organization's root URL]/data/Customers?$format=json | List all the customers in a JSON format that can be used to interact with JavaScript clients. |
The OData protocol supports many similar filtering and querying options on entities.
Authentication
OData sits on the same authentication stack as the server.
Tips and tricks
Run multiple requests in a single transaction
The OData batch framework uses changesets. Each changeset contains a list of requests that should be treated as single atomic unit. In other words, either all the requests are run successfully or, if any request fails, none of the requests are run successfully. The following example shows how to send a batch request that has a list of requests in a single changeset.
The SaveChangesOptions.BatchWithSingleChangeset option in SaveChanges() helps guarantee that all requests are bundled into a single changeset.
public static void CreateProductColors(Resources context)
{
var productColorsCollection = new DataServiceCollection<ProductColor>(context);
var color1 = new ProductColor();
productColorsCollection.Add(color);
color1.ColorId = "New Color1"; // set any other properties needed
var color2 = new ProductColor();
productColorsCollection.Add(color1);
color2.ColorId = "New Color2"; // set any other properties needed
context.SaveChanges(SaveChangesOptions.BatchWithSingleChangeset);
}
Prevent unset records from being posted when you use an OData client
When you create a new record by using an OData client, as shown in example 1, properties that aren't set are included in the body of the request, and default values are assigned to them. To prevent this behavior and post only properties that are set explicitly, use the SaveChangesOptions.PostOnlySetProperties option in SaveChanges(), as shown in example 2.
Example 1
public static void CreateVendor(Resources context)
{
var vendorCollection = new DataServiceCollection<Vendor>(context);
var vendor = new Vendor();
vendorCollection.Add(vendor);
// set properties
context.SaveChanges();
}
Example 2
public static void CreateVendor(Resources context)
{
var vendorCollection = new DataServiceCollection<Vendor>(context);
var vendor = new Vendor();
vendorCollection.Add(vendor);
// set properties
// Save specifying PostOnlySetProperties flag
context.SaveChanges(SaveChangesOptions.PostOnlySetProperties);
}
Handling duplicate names between enums and entities in metadata
There are instances where enums and entities share the same name. This name duplication results in OData client code generation errors. To recover from this error, the helper code in gitHub https://github.com/Microsoft/Dynamics-AX-Integration/blob/master/ServiceSamples/ODataConsoleApplication/MetadataDocumentValidator.cscan be used to identify duplicate name instances that must be removed. The generated metadata document can be used for further processing of the Odata logic on the client side.